The objective of the security architecture is to enable you to maintain your security posture when running your business-critical EBS and associated applications in the Oracle Cloud. Even though you may be reducing the overhead of building and maintaining data center infrastructure, you still need unparalleled control and transparency over what you’re running in the cloud.
Outcomes this architecture can provide:
- Ensure E-Business Suite and associated data assets are completely isolated from other tenants’ workloads and Oracle’s staff so to limit the effect of noisy neighbors and prevent lateral movement of attacks
- Protect your internet-facing applications from cyberattacks
- Encrypt your data at rest and in transit in a way that allows you to meet your security and compliance requirements
- Segregate operational responsibilities and restrict access to cloud services in order to reduce risk associated with malicious and accidental user actions
- Be able to leverage existing security assets, identity provider and other third-party security solutions to access and secure your application and data
- Audit and monitor actions taken on your cloud resources so that you can meet audit requirements
- Demonstrate compliance readiness to internal security and compliance teams, end-customers, auditors and regulators
Security tools and controls covering core IAM, networking, compute, data management etc from OCI, can help you run critical workloads and supporting databases, securely on our cloud without having to rebuild your security posture.
Network Security Reference Architecture
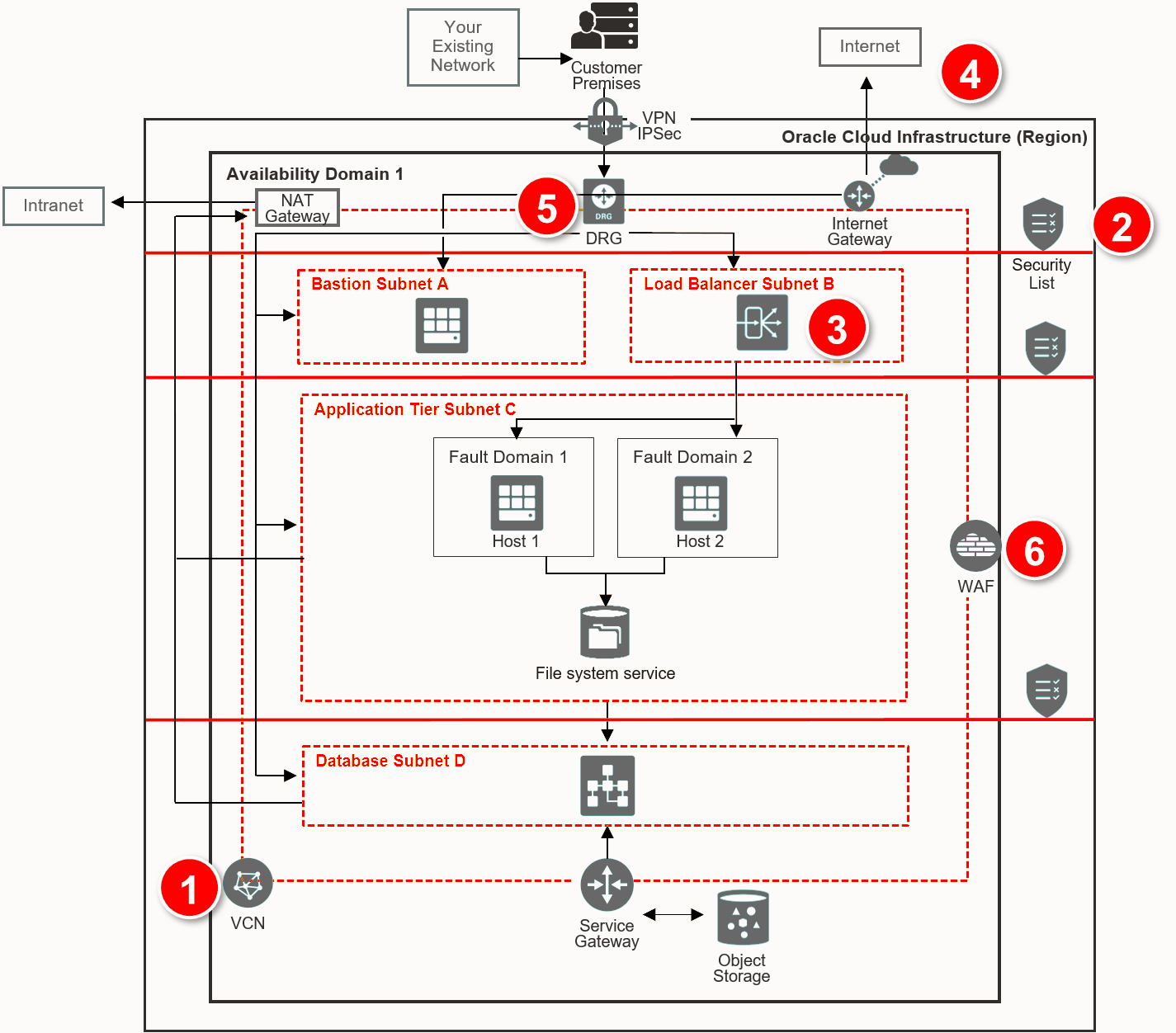
Virtual Cloud Network (1): Provides isolation for E-Business Suite from any other workload on Oracle Cloud. Subdivide using subnets and apply security rules to isolate and control access to resources.
Internal firewalls (2): A security list provides a virtual firewall for each tier, with ingress and egress rules that specify the types of traffic allowed in and out.
Secure load balancing (3): TLS 1.2 is supported by default to securely balance traffic within the implementation and from external connections
Secure connectivity to internet (4): Internet bound traffic to/from a VCN must pass through an Internet Gateway. Virtual routing tables can be implemented with private IP addresses for use with NAT and 3rd party firewall devices.
Secure connectivity to your data center (5): Traffic can be routed through a DRG for private traffic. It is used with an IPSec VPN or FastConnect connection to establish private connectivity to your premises or other cloud network.
Protect web applications (6): Oracle provides a Web Application Firewall (WAF) service that inspects any request from the web application server to end user.
Server Isolation (Single-tenant or multi-tenant environments)
VM compute shapes
- Dedicated VM hosts offer single tenant option
- Multi-tenant shapes have security-hardened hypervisor for strong isolation between customers
Bare Metal compute shapes
- Single-tenant shapes with no Oracle managed hypervisor. Oracle staff have no access to memory nor local NVMe storage while running
- Not recommended for database tier
Compute instances security configuration
- VM instances are architected with least privilege mechanisms. It is imperative to securely configure compute instances to maintain security of EBS applications running on them.
When it comes to server isolation, OCI offers choice. The Oracle Cloud Infrastructure Compute service’s dedicated virtual machine host feature provides you with the ability to run your Compute virtual machine (VM) instances on dedicated servers that are a single tenant and not shared with other customers. This enables scenarios where you have compliance and regulatory requirements for isolation that prevent you from using shared infrastructure. If you have more flexible requirements for EBS, the multi-tenant VM shapes leverage a security-hardened hypervisor that provides strong isolation between customers. And all compute instances are architected with least privilege mechanisms. It’s also important to securely configure compute instances to maintain security of your EBS applications running on them. OCI offers optional CASB service to help you ensure secure configuration of cloud resources.
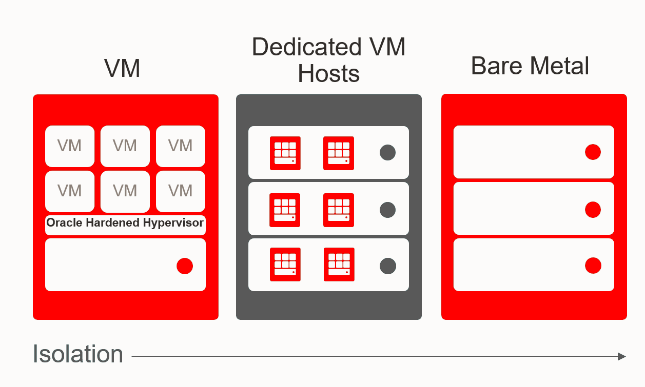 If you require the most complete workload and data isolation at the server level for app tier security and/or performance requirements, you can leverage bare metal compute shapes. These shapes are single tenant so they offer consistently high performance and are immune to noisy-neighbor issues. There is also no Oracle managed hypervisor and Oracle staff have no access to memory nor local NVMe storage while the instance is running.
If you require the most complete workload and data isolation at the server level for app tier security and/or performance requirements, you can leverage bare metal compute shapes. These shapes are single tenant so they offer consistently high performance and are immune to noisy-neighbor issues. There is also no Oracle managed hypervisor and Oracle staff have no access to memory nor local NVMe storage while the instance is running.
Bare metal shapes are not recommend for the database tier because RAC is recommended for EBS and RAC only runs on VMs.
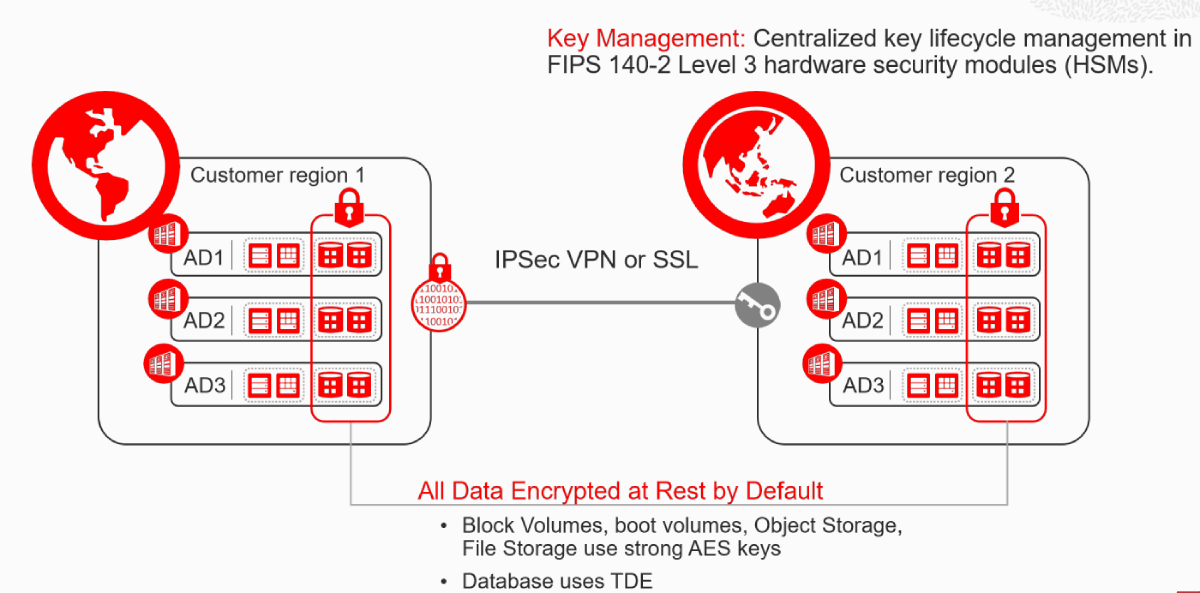
Data Encryption
By default, all data that customers store with any of Oracle Cloud Infrastructure’s storage or data management services, including Block Volumes, boot volumes, Object Storage, File Storage, and Database, is encrypted at rest using strong AES keys or TDE in the case of database encryption.
Key Management: For customers that require the ability to control their own cryptographic keys for security or compliance purposes, we offer Oracle Cloud Infrastructure Key Management. With Key Management, you can centralize key lifecycle management in FIPS 140-2 Level 3 hardware security modules (HSMs).
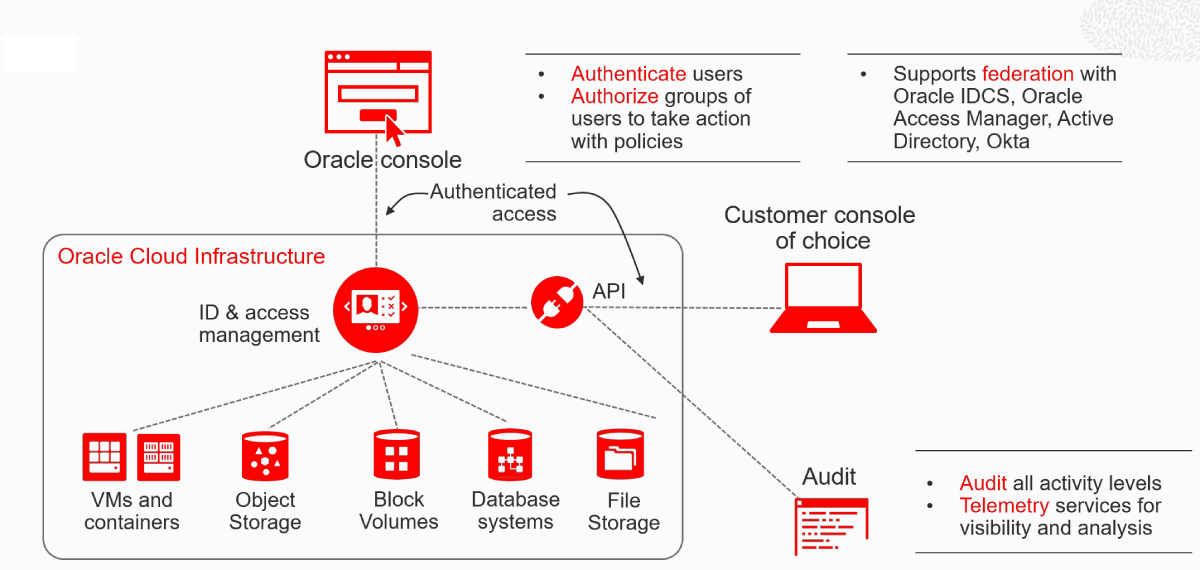
Identity, Access Management and Audit
With the IAM architecture, you can group and isolate resources according to your organizational structure and hierarchy, control who has access to cloud resources, what type of access a group of users has, and to which specific resources.
With IAM you can:
- Securely isolate cloud resources based on organizational structure
- Authenticate users to access cloud services via browser interface, REST API, SDK or CLI
- Authorize groups of users to perform actions on appropriate cloud resources
- Authorize application instances to make API calls against cloud services
- Oracle IAM supports federation with Oracle Identity Cloud Service (IDCS), Microsoft Active Directory Federation Services (AD FS), Okta, and any other SAML 2.0 compliant identity provider including Oracle Access Manager (OAM).
When you sign up for Oracle Cloud Infrastructure, your tenant administrator account is automatically federated with Oracle Identity Cloud Service. Federating with Oracle Identity Cloud Service automatically allows you to have a seamless connection between services without having to create a separate username and password for each one. You may be leveraging the application’s own security mechanisms to provide authentication with integrated applications on-premises that leverage LDAP, OAM or other 3rd party solutions. Therefore, we recommend federating your favorite IDP with IDCS which will automatically provide federation for all Oracle cloud offerings.
Oracle automatically records calls to all supported Oracle Cloud Infrastructure public application programming interface (API) endpoints as log events. Currently, all services support logging by our Audit service. You can leverage this data to perform diagnostics, track resource usage, monitor compliance, and collect security-related events.
OCI Compliance Certifications
And depending on where you do business and industry-specific practices, you may need to demonstrate compliance readiness to internal teams and to external auditors. Oracle continually engages with external assessment entities and independent auditors to meet a broad set of international and industry-specific compliance standards for service deployments on our cloud.

Gartner in its report recommends to engage accredited Oracle expert service providers to optimize strategy, architecture, cost, migrations and management.
Creating a secure environment for mission critical applications will require involvement of key stakeholders with specialized skillsets. It is highly recommended to leverage partners certified with Oracle Cloud Service Provider Expertise (CSPE) Partners to ensure you avoid any roadblocks in your cloud migration journey and avoid the threat of data breaches on cloud.

